We just walked another site for a newer client who’s upgrading their card access control to a modern, cloud-based system.
Like a lot of businesses, they weren’t planning a full upgrade at first. Their previous S2 system failed, and they needed to get doors working again—fast.
So they called a local locksmith.
The locksmith replaced the card readers with a prox.pad – Integrated Proximity & Controller. On the surface, it looked like a simple, cost-effective way to restore access.
But when we evaluated the system, it was clear the “quick fix” created real security and reliability risks.
The hidden risk of 125 kHz low-frequency credentials
Many integrated proximity controller/reader devices rely on 125 kHz low-frequency credentials.
The problem is that 125 kHz prox credentials are widely known to be:
- Easy to clone with readily available tools
- Vulnerable to spoofing
- A weak link for any organization that needs strong accountability and access control integrity
If your credential technology can be copied easily, your access control system can’t reliably answer the most important question: Who actually opened that door?
A bypass most people don’t expect: magnets
There’s another issue that doesn’t get enough attention.
Certain integrated controller/reader setups can be bypassed with a magnet under the wrong conditions.
That’s not a theoretical concern. It’s a practical, real-world vulnerability that can show up when the wrong hardware is chosen—or when it’s installed without a full understanding of physical electronic security best practices.
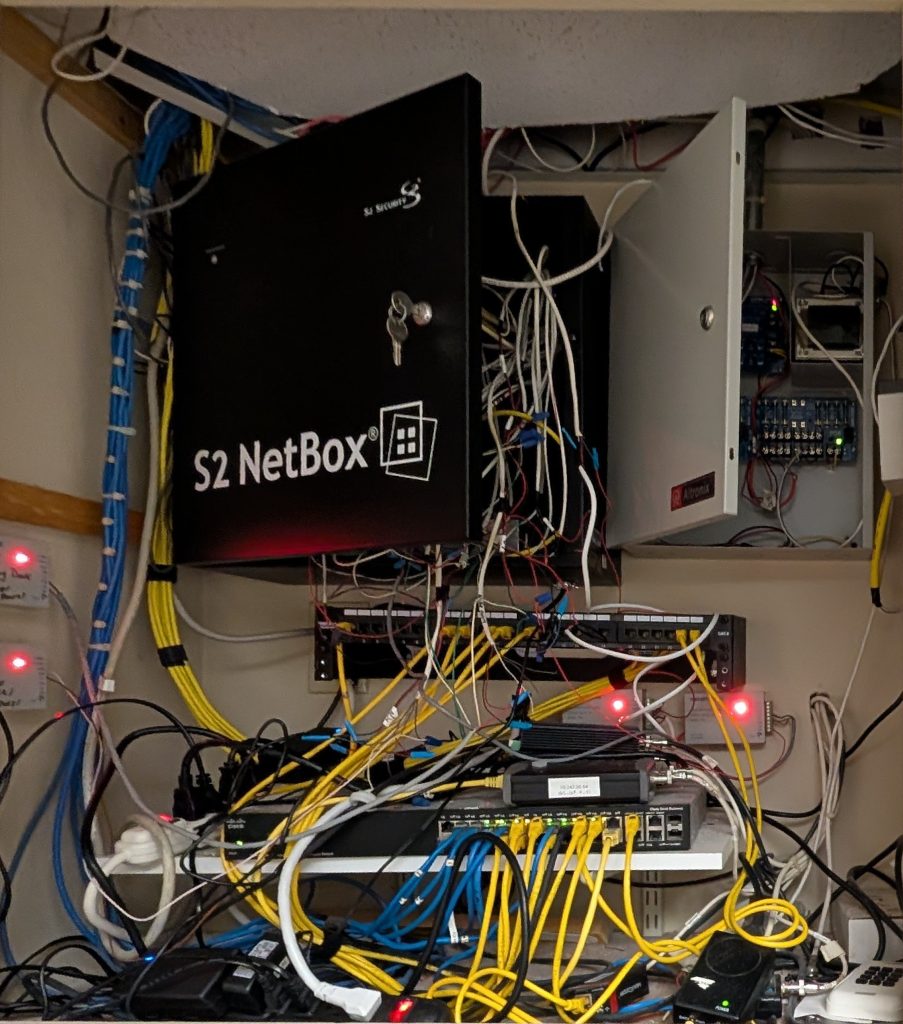
The installation told the bigger story
When I looked at the power supply and overall installation, it was obvious this was a “make it work” job—not a “make it secure and maintainable” job.
Here’s what we found:
- The old control panel was left on the wall instead of being properly removed and decommissioned
- Reader wiring was pulled through the door—a lazy shortcut that can create reliability issues and increase tampering risk
Access control isn’t just about the reader on the wall. It’s the entire chain:
- Door hardware and locking method
- Secure controller placement
- Proper enclosures and power supervision
- Correct wiring methods and protection
- Clean terminations, labeling, and documentation
When those fundamentals are ignored, you can end up with a system that functions day-to-day—but is far easier to defeat.
“Licensed” doesn’t always mean “current”
To be clear: locksmiths are licensed to install card access in New Jersey.
The issue is that card access today isn’t just “hardware on a door.” Modern systems sit at the intersection of:
- Life safety and building codes
- Physical electronic security best practices
- Cybersecurity best practices (especially with cloud-based platforms)
If an installer isn’t staying current on these areas, you can end up with a system that’s out of spec, vulnerable, or difficult to support—especially when it’s time to expand, audit, or troubleshoot.
What a proper cloud-based upgrade should deliver
A cloud-based access control upgrade should do more than give you a new app.
It should:
- Move you away from easily cloned credential technology
- Improve security at the door (not just in software)
- Ensure wiring, power, and enclosures are installed correctly
- Reduce bypass and tampering opportunities
- Align with modern cybersecurity expectations
- Give you clean administration, audit trails, and scalability
If your system was “patched” after a failure, it’s worth a review
If your access control was repaired quickly after a failure, that’s understandable.
But it’s smart to treat that repair as temporary—then have the system evaluated by a security integration professional who designs for security, code compliance, and long-term reliability.
If you’re not sure what credential type you’re using, whether your doors can be bypassed, or whether your wiring and power are installed properly, we can walk the site and give you a clear, professional assessment.
Next Step: Upgrade to Secure, Compliant Cloud Access Control
If you’re considering a cloud-based access control system—or you suspect your current setup was pieced together after a failure—reach out.
We’ll help you upgrade the right way: secure, clean, compliant, and built to last.
